Aliro: Real World Deployments of Entanglement-based Secure Networks

Multipurpose entanglement-based secure network trials, pilots, and deployments are growing across various enterprises and organizations. This article discusses three implementations. For more detailed information on use cases and applications, see the on-demand webinar Why Quantum Networks, Why Now?.
Energy and Telecommunications Organization: EPB
EPB launched a broadband data network on its fiber infrastructure over 10 years ago, and it has been a huge commercial success. Chattanooga was nicknamed “Gig City” and the economy has benefited tremendously from this advanced network. Now EPB is moving forward to the next phase of networking: quantum networking. This year EPB launched the first commercial quantum network in the US, EPB Quantum Network℠ powered by Qubitekk. Paying subscribers will get access to an entanglement- based network that is more advanced than any found in top universities or national labs.
Quantum networks have several early use cases, the most prominent being secure communications using entanglement (often called “physics-based security”). EPB customers will include researchers, companies developing new cybersecurity products, as well as enterprises in financial services, pharma, and energy where secure communications is a high priority. Chattanooga is now rebranding as “Gig City goes Quantum”, and EPB believes their quantum network, as it expands and new applications are found, will have a similar positive impact on their local economy.
EPB’s quantum network, shown schematically below, includes a network operations control center (CC), two equipment hubs (EH), and 10 quantum nodes (QN) for end user access to the quantum network. These are all interconnected via existing EPB high-speed fiber optical infrastructure.
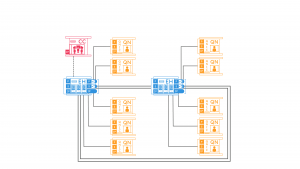
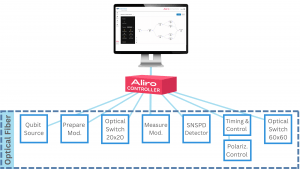
As shown below, AliroNet™ centralizes, automates, and simplifies control of EPB Quantum Network℠ which includes more than 30 quantum devices.
The multitenant Aliro Orchestrator shown below provides a graphical user interface for quantum network operators and end users of the quantum network.
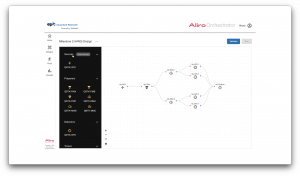
End users are able to select from a list of quantum components and click, drag, and drop devices to easily design their quantum network. AliroNet™ then validates their quantum network design for correctness.
The user can configure quantum network parameters of the network and specific components inside the network. This includes node and link configurations and an option to view logs
AliroNet™ prepares the quantum network devices with the desired configuration and initializes the application or test based on the design and parameters then runs the application or test on the actual network for the duration set by the user. Once the experiment is complete, AliroNet confirms and reports the results followed by a deinitialization and reset of the quantum network devices.
For a video explaining this in more detail, along with a demonstration of the Aliro Orchestrator, please see this short video.
National Research Lab
Government funded research labs across the US are building entanglement-based secure network testbeds. Each lab has unique requirements for their entanglement-based secure network – for example, different hardware, software, control, and network protocol needs. There are other differentiators as well, but they share an essential common goal: to accelerate the progress of entanglement-based secure networks and technologies.
The lab in this case has built its entanglement-based secure network testbed and experimental facility which is open to their user community The network leverages orchestration and control software to simplify management enabling seamless use of the network for both internal and external users. Access control and multitenancy is vital for any network, and especially those used by multiple organizations.
The networks will eventually be capable of expanding across multiple cities and will connect with other similar networks as a wide area network. There are two primary methods for doing this:
- quantum repeaters to enable longer distance entanglement-based links when they become commercially available.
- free space optical components, which could be terrestrial with fixed laser telescopes, or non-terrestrial with satellites to connect entanglement-based secure networks to one another.
These advances will also lead to the building of the Quantum Internet.
Many national research labs have taken a waterfall approach to building their quantum networks. A majority of their resources and focus have gone to building, acquiring, and developing the hardware necessary for entanglement-based secure networks. In many cases, how they will meet the software requirements of their network isn’t considered until the hardware is in place. The most advanced quantum networks globally are those networks that have deployed hardware and software simultaneously. This has proven to be the most efficient and effective approach. Engaging with entanglement-based secure network software vendors will accelerate progress of these testbeds without adding more work and responsibility to already very busy labs.
Intelligence organization
Intelligence organizations can extract tremendous value from entanglement-based secure networks, creating Quantum Secure Communication (QSC) channels and taking advantage of the multipurpose nature of these networks for distributed quantum sensing and networking quantum computers. Building metro area networks today to safeguard communication at individual locations between locations provides immediate value to the organization and is a vital step toward developing global Quantum Secure Communications.
The intelligence organization in this case is implementing its entanglement-based secure network as a series of evolving topologies.
Step 1: Deploy a local area entanglement-based secure network in the metro area at a single location to provide provably secure communications via QSC between buildings at the location.
Step 2: Deploy a second local area entanglement-based secure network which will secure its location in a distant location. These two distant locations will be connected classically and use post quantum cryptography to offer additional security. Post quantum cryptography (PQC) is a purely classical solution offering additional but not provable security. As the entanglement-based secure networks scale, PQC and QSC can be used together to provide security in depth.
Step 3: Expand to an entanglement-based secure wide area network by using terrestrial and non-terrestrial free space components. The metro quantum network scales from a metro area network to a wide area network through the use of laser telescopes and via satellite using quantum secure communications to secure connections between locations.
An additional local area entanglement-based secure network will be implemented overseas and connected to the metro quantum network classically, utilizing PQC to secure the communication.
Quantum repeaters will be implemented as they become commercially available. The intelligence organization must choose where and when it will use scaling technologies such as quantum repeaters, terrestrial and non-terrestrial optical free space components, etc. Using a quantum network simulator can help to ensure the most effective and efficient method is used. In this way, the network will evolve into a global entanglement-based secure network by the end of the decade.
This intelligence organization is focused on quantum secure communications, but planning to utilize other entanglement-based secure network use cases. As its entanglement-based secure network scales, the organization will explore, test, and use applications of distributed quantum computing and sensing for additional offensive and defensive capabilities.
These examples show how real world entanglement-based secure networks are being implemented across a variety of organizations, each with different goals for their network. The recent influx of activity and investment in entanglement-based secure networks should be seen as no surprise: entanglement-based secure networks are the future of secure networks, offering remarkable innovative use cases in addition to robust network security. Exploring entanglement-based secure network use cases can pay dividends for organizations and enterprises that make the investment before their competitors. For more details about the examples explored here, see the on-demand webinar Real World Quantum Network Deployments
SPONSORED: Aliro



















